The weakest link in security is the human, and criminals are getting a lot better at the kind of phishing emails they send. They don’t have to crack systems, they can crack you by getting you to give up your credentials. Crooks have figured out that if they spend a little extra time proofreading emails and putting an official logo on them, it’s often enough get even intelligent users to click through to a fake page and give up passwords. Though not widely disclosed, the “hacks” of prominent news organizations websites and social media feeds by the Syrian Electronic Army were simply well-crafted phishing emails. The malware filters on your email don’t always catch them.
This one got through and someone actually took the time to make it look nice and proofread it. It could easily have come from your bank or other financial institution. I annotated it just to show what to look for.
If any of your web services have 2 factor auth, you should set them up. Google and Yahoo! accounts (i.e. Gmail, Docs, Yahoo Mail), social networks (Facebook, Twitter, etc) have it. Sadly, your bank does not even though it would make it extremely difficult for a remote attacker to access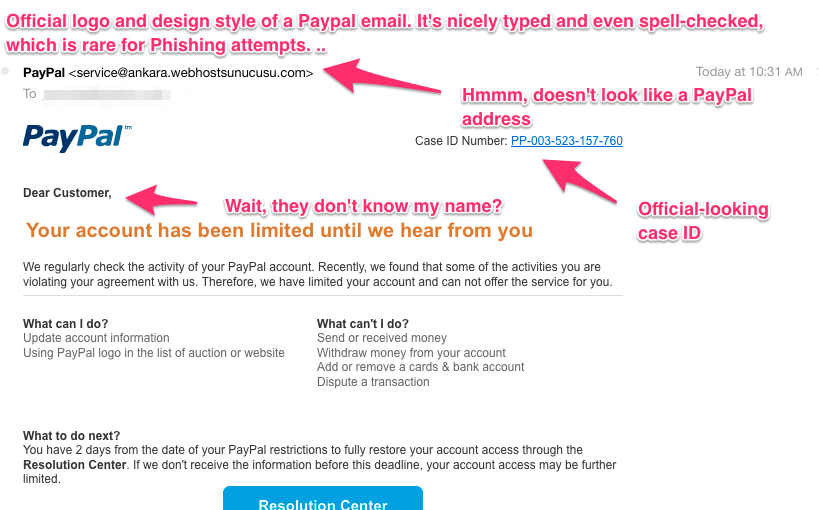 your account.
your account.
